In a little over a decade, the World Wide Web has evolved from purely static information repositories into highly functional applications that process sensitive data and perform powerful actions with real-world consequences. During this development, several factors have combined to bring about the weak security posture demonstrated by the majority of today’s web applications.
Most applications face the core security problem that users can submit arbitrary input. Others have vulnerabilities wherein it is possible to bypass user authentication. Every aspect of the user’s interaction with the application may be malicious and should be regarded as such unless proven otherwise. Failure to address these problems can leave applications vulnerable to attack in numerous ways.
As a silver lining, as the threats have increased, so have the efforts of the community to decrease the exploitation. The first is to change the culture in the developer community on their routine way of working and second is to create tested libraries to help programmers write applications securely. The testing software also helps to plug the vulnerabilities before they hit the production environment. Further, the Secure SDLC process, with automated controls, should be used by the development fraternity has also gained coverage and seeing partial implementations.
Even regulators have understood the importance of having a “secure application” and have included this in various standards as a mandatory control. To keep the scope limited, I will list down a few actions that are required to ensure GDPR compliance. For people who are new to the word GDPR, well, it stands for “General Data Protection Regulation”, published by EU, and is applicable to all the residents of the region. All the organizations doing any business in the region, irrespective of where they are storing their data, fall under the purview. (Read more about GDPR at https://www.eugdpr.org). The following set of best practices help create Web Applications manage the risk of non-compliance.
- Security by design: This is one of the core aspects of the new GDPR. The expectation is that data security and privacy are built into the application or system from the outset. Security and privacy should be included in the planning stages of the Software Development Life Cycle (SDLC) for effective application security. A sample framework is as shown below:
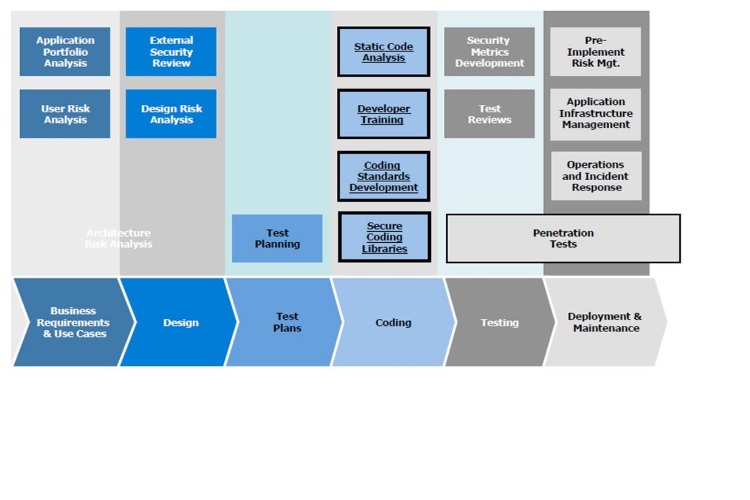
- Risk and security: As part of the EU GDPR, organizations are required to “ensure a level of security appropriate to the risk,”. This includes encrypting personal data but also the pseudonymization of personal data in order to mask the most identifying fields within data records. Organizations are also expected to set up a process for regularly assessing, testing security practices and running an effective Vulnerability Management program.
- The principle of least privilege: To adhere to the new EU GDPR, organizations also need to practice the principle of least privilege, meaning that they need to set up their systems and processes with the idea that only those who need access to certain data are allowed to have it. Organizations should regularly ‘clean house’ and remove any data that it no longer requires to keep.
The author is CISO at Birlasoft


